OpenID Connect Authentication
Before using OpenID Connect, your site must implement or have access to an OpenID Connect Provider (https://openid.net).
Trihedral does not endorse or recommend any provider over another.
The VTScada documentation does not, and can not, provide instructions for the configuration of an OpenID Connect Provider.
OpenID Connect logons are supported only on the VTScada Anywhere Client.
OpenID Connect is a standard for user-authentication. If enabled in VTScada, operators can connect to the VTScada Anywhere client using their OpenID Connect credentials. This may be useful at sites where a user must logon once, then access several business applications throughout their day without needing to logon again. It can also provide enhanced security through the use of two-factor or multi-factor authentication. Refer to the OpenID Foundation website for further information.
OpenID Connect accounts are mapped to each user's VTScada account by matching the content of a claim![]() In OpenID Connect, each field of information describing a user's account is referred to as a "claim". field from the provider to the VTScada account names. Every user must have both an OpenID Connect account and a VTScada account.
In OpenID Connect, each field of information describing a user's account is referred to as a "claim". field from the provider to the VTScada account names. Every user must have both an OpenID Connect account and a VTScada account.
If you have implemented Windows Security Integration (WSI), the claim can be "email", assuming that the email addresses match the Active Directory user principal names. Because VTScada account names can include @ symbols only when WSI is enabled, some other claim that specifies the VTScada account name must be used if WSI is not enabled. It may be necessary to configure your provider to add an appropriate claim field and populate it with your user's VTScada account names.
You will continue to manage privileges and roles within VTScada. OpenID Connect is used to authenticate users when signing in. It does not specify what they can or cannot do within an application.
As with any Internet and Mobile device connection, you must first enable security, create at least one account with the Thin Client Access privilege, and you must configure a VTScada Thin Client Server with your application made available through a named realm. An SSL (TLS) certificate is strongly recommended.
If a company portal is being used to direct users to the VTScada Anywhere Client then Anywhere Client URLs can be converted into URLs that will automatically initiate an OpenID Connect login. For example https://example.vtscada.com/realm/app/ANYWHERE/Page would become https://example.vtscada.com/realm/app/ANYWHERE-OIDC/Page
The redirect URIs sent by VTScada to the OpenID Connect provider take the form "https://hostname/vtscada/oidc/return" where hostname matches the address of the VTScada Thin Client Server. This must be a secure (https:) connection.
All of the possible hosts used to access your Anywhere Client servers must be accepted or registered with the OpenID Connect Provider.
Sign in using OpenID Connect
OpenID Connect is available only for the VTScada Anywhere Client. The following steps assume that you have finished configuration and now signing in as an authorized user.
- Use your preferred browser to navigate to your Anywhere Client's sign in page.
- Once there, you should see two options, the regular username / password route to sign in, and below it the Sign In with OpenID Connect button. If not, your system is not yet configured.
- Select the OpenID Connect button, which should redirect you to your configured OpenID Connect provider.
- Sign in with the username and password assigned for your enterprise's OpenID applications.
(Not required if you are already signed in to another of your enterprise's applications. You may need to provide further authentication, for example if two-factor authentication has been configured.)- Upon successful authentication, the Anywhere Client should start and you will be signed in.
OpenID Configuration
All of the URLs configured in the OpenID Connect settings dialogue must be HTTPS, using a certificate trusted by the system running VTScada.
OpenID Connect is enabled and configured within the Administrative Settings dialog:
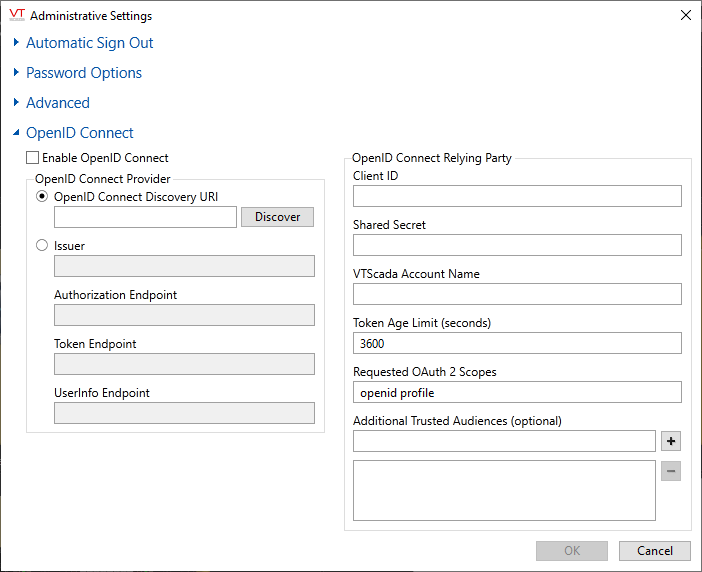
Enable OpenID Connect
You can choose to allow connections using OpenID Connect, standard VTScada username and password connections, or both.
If you disable both of OpenID Connect and remote sign-in using VTScada account credentials, users cannot connect through Internet or Mobile clients, remote data access (REST) or SOAP services.
Ensure that Enable OpenID Connect is selected before proceeding to the other options in this dialog.
OpenID Connect Provider
Enter the URI (Uniform Resource Indicator) to the metadata endpoint of your OpenID Connect provider. This will have a form similar to: https://your.provider.com/adfs/.well-known/openid-configuration (*)
After entering the URI, select the Discover button. The Issuer and Endpoint fields will be populated automatically from the information found there.
Alternatively, you may enter this information yourself, if known.
(*) "adfs" refers to Active Director Federation Services, provided by Microsoft. Your URI may vary.
Client ID
The Client ID that you have registered with your OpenID Connect provider for use with VTScada.
Shared Secret
The Shared Secret provided by the OpenID Connect provider for use with VTScada. Note that client certificates are not supported.
VTScada Account Name
Do not enter a VTScada Account Name.
This field specifies the claim that contains the VTScada account name and it will vary depending on how your OpenID Connect provider is configured. This may be "email", or "upn" etc.
Refer to the notes earlier in this discussion for more information about mapping OpenID Connect accounts to VTScada accounts.
Token Age Limit
Sets the maximum accepted age of tokens issued by the OpenID Connect provider.
Requested OAuth 2.0 Scopes
Scope is used to limit the authorization granted to the client by VTScada.
Additional Trusted Audiences
As part of the OpenID Connect process, you must check several things. One of these is that the token was issued for VTScada and is not one issued for another application and substituted in. This is done by the OpenID Connect Provider sending a list of audiences the token is intended for, and in some situations this can be a list of several audiences. VTScada must have a list of any other audiences that may be included in the ID token and any ID tokens received by VTScada that contain audiences not in this list will be rejected.
The entries added to the list are other Client IDs besides VTScada that are considered trustworthy.
This is unlikely to be required for most installations and may be left blank.
Enable - property controlling whether OpenID Connect authorizations are allowed.
RemoteAuthMethodsDisallowed - property controlling whether username/password authorizations are allowed on VTScada Thin Client Servers.
Workstation-Specific Properties - Includes an example of setting RemoteAuthMethodsDisallowed for one VTScada Thin Client Server but not another. An example is provided in the topic,
